Welcome to the ultimate guide for securing your WordPress website in 2025. As we step into a new era of online innovation, cyber threats such as Japanese malware attack have become more sophisticated, and safeguarding your WordPress site has never been more crucial. Whether you’re a blogger, entrepreneur, or developer, your website’s security is the foundation of your online presence.
Did you know that WordPress powers over 43% of the internet? This dominance, while impressive, makes it a prime target for hackers. From data breaches to malware injections, the consequences of inadequate security measures can be devastating—not just for you but for your visitors as well.
In this updated guide, we’ll explore a comprehensive list of 40 WordPress Security Best Practices in 2025. These practices are grouped into four key categories to help you systematically secure your website:
- Core Practices: These essential steps form the foundation of your website’s security.
- File and Access Security: Protect the files and configurations that make up your site.
- Advanced Measures: Take your security to the next level with expert techniques.
- Proactive Monitoring and Education: Stay ahead of potential threats with regular monitoring and user education.
Ready? Let’s dive in!
Core Practices: Building a Strong Foundation for WordPress Security Best Practices
Securing your WordPress site starts with establishing a robust foundation. The following 10 core practices are the building blocks of a secure website. By implementing these steps, you’ll address the most common vulnerabilities and significantly reduce the risk of attacks.
1. Update WordPress Core, Plugins, and Themes
Your first line of defense is keeping everything up to date. WordPress regularly releases updates to address vulnerabilities and improve performance. The same goes for plugins and themes. Set up automatic updates or schedule manual checks to ensure your site is running the latest versions.
Pro Tip: Test updates on a staging site before applying them to your live site to avoid potential conflicts.
2. Use Strong Passwords
Weak passwords are an open invitation to hackers. Use a mix of uppercase and lowercase letters, numbers, and symbols to create strong passwords for all accounts, especially those with administrative access.
Example: A password like P@ssw0rd2025! is far more secure than admin123.
3. Enable Two-Factor Authentication (2FA)
Two-factor authentication (2FA) adds an extra layer of security by requiring a second verification step after entering your password. Use plugins like miniOrange to enable 2FA for your WordPress login.
4. Use Trusted Themes and Plugins
Always download themes and plugins from reputable sources such as the WordPress repository or well-known developers. Avoid nulled or pirated versions, as they often contain malicious code.
Reminder: Check reviews, ratings, and update frequency before installing any theme or plugin.
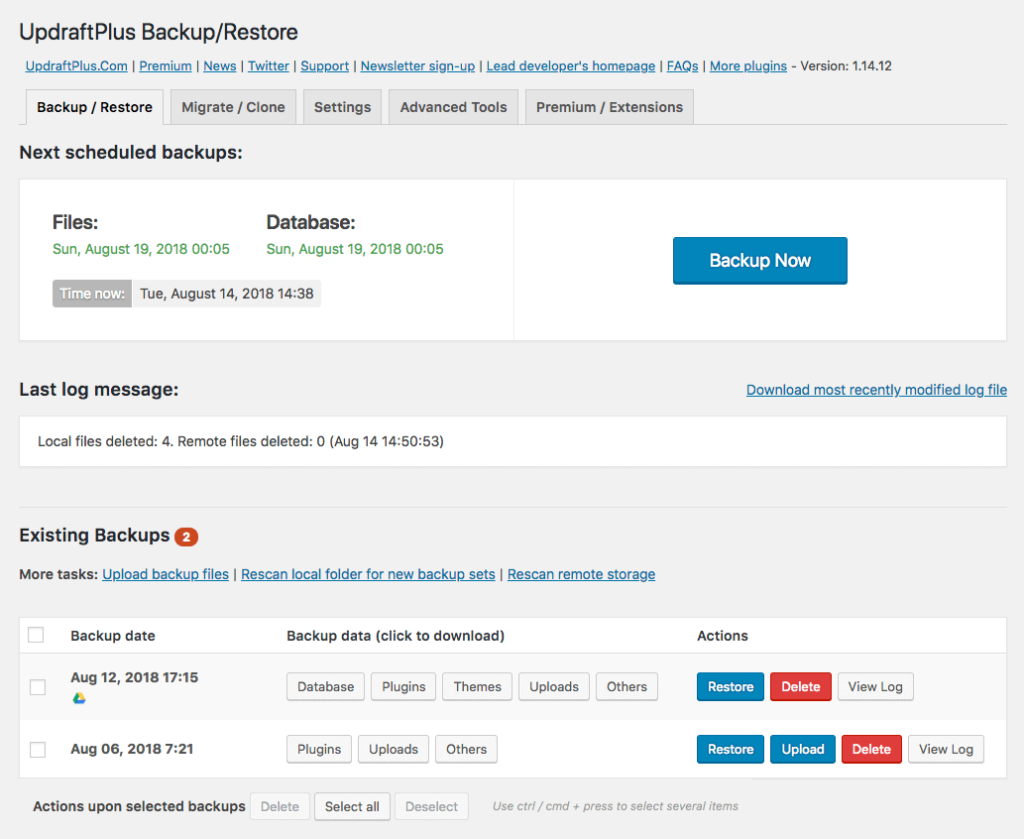
5. Back Up Your Website Regularly
Even the best security measures can’t guarantee 100% protection. That’s why regular backups are non-negotiable. Use plugins like UpdraftPlus or Jetpack VaultPress Backup to automate daily or weekly backups. Store backups offsite, and periodically test them to ensure they can be restored successfully.
6. Install a Firewall Plugin
Firewalls act as a shield, blocking malicious traffic before it reaches your website. Plugins like Wordfence or Sucuri offer excellent protection by monitoring and filtering traffic in real time.

7. Implement HTTPS with SSL Certificates
An SSL certificate encrypts the data exchanged between your website and its visitors, ensuring sensitive information like passwords and personal data is protected. Most hosting providers offer free SSL certificates. Make sure your site uses HTTPS instead of HTTP.
8. Disable XML-RPC
XML-RPC is a feature that allows remote access to your WordPress site. Unfortunately, it’s also a common target for brute-force attacks. Disable it unless you absolutely need it by using a plugin or adding custom code to your functions.php file.
Here is a nice article that explains how to disable XML-RPC in WordPress.
9. Limit Login Attempts
By limiting failed login attempts, you can prevent brute-force attacks from overwhelming your site. Use plugins like Limit Login Attempts Reloaded or Loginizer to block IPs after multiple unsuccessful login attempts.
10. Change the Default Login URL
The default WordPress login URL, /wp-login.php, is well-known and often targeted by bots. Use a plugin like WPS Hide Login to customize this URL and make it harder for attackers to find your login page.
File and Access Security: Fortifying Your WordPress Backend
File and access security are critical to safeguarding the inner workings of your WordPress site. Unauthorized access or file manipulation can compromise your website’s integrity, functionality, and data. Here’s how to fortify your site against such threats.
11. Disable File Editing in WordPress Dashboard
Prevent any admin user from editing files directly through the WordPress dashboard by adding the following line to your wp-config.php file:
phpCopy codedefine('DISALLOW_FILE_EDIT', true);
This simple change removes the file editing options from your dashboard, blocking potential exploits.
12. Set Proper File and Folder Permissions
Incorrect file and folder permissions can expose your site to unauthorized access. Set directory permissions to 755 and file permissions to 644. These permissions strike a balance between functionality and security.

Pro Tip: Use an FTP client or your hosting control panel to check and modify permissions.
13. Restrict Access to wp-admin
Limit access to the wp-admin directory by implementing IP whitelisting. This ensures that only specific IP addresses can access the administrative area of your WordPress site.
How-To: Add the following code to your .htaccess file:
apacheCopy code<Files wp-login.php>
Order Deny,Allow
Deny from all
Allow from 123.456.78.90
</Files>
Replace 123.456.78.90 with your IP address.
14. Secure wp-config.php
The wp-config.php file contains sensitive information, such as database credentials. Move this file to a higher directory level, where it is inaccessible to public users, and restrict its permissions to 400 or 440.
15. Disable Directory Indexing
Prevent attackers from viewing a directory’s contents by disabling directory indexing. Add the following line to your .htaccess file:
apacheCopy codeOptions -Indexes
16. Monitor File Changes
Unauthorized file changes are a telltale sign of a security breach. Use security plugins like Wordfence or Sucuri to monitor and alert you of any changes to your WordPress files.
17. Block Hotlinking
Hotlinking allows others to directly link to your resources, consuming your bandwidth. Block hotlinking by adding this code to your .htaccess file:
apacheCopy codeRewriteEngine on
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^https://(www\.)?yourdomain.com/ [NC]
RewriteRule \.(jpg|jpeg|png|gif)$ - [F]
Replace yourdomain.com with your actual domain name.
18. Add Security Keys and Salts
WordPress uses security keys and salts to encrypt session and cookie data. Update these keys regularly by generating new ones from the WordPress Salt Generator and replacing them in your wp-config.php file.
19. Restrict Theme and Plugin Installation
To prevent unauthorized installation of themes and plugins, add the following code to your wp-config.php file:
phpCopy codedefine('DISALLOW_FILE_MODS', true);
This measure is especially helpful if you allow multiple administrators on your site.
20. Use Content Delivery Networks (CDN)
CDNs like Cloudflare add an extra layer of security by distributing your content across multiple servers and protecting against DDoS attacks. Many CDNs also offer features like Web Application Firewalls (WAF) and malware scanning.
Advanced Measures: Elevating Your WordPress Security
Once you’ve implemented core and file security practices, it’s time to take your WordPress security to the next level. These advanced measures provide an extra layer of protection against sophisticated attacks, ensuring your site is as secure as possible.
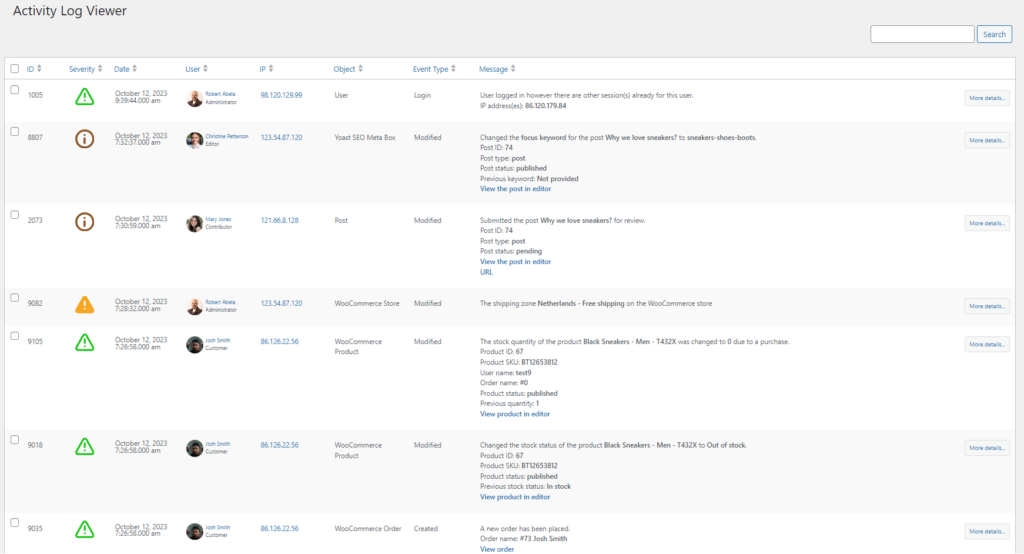
21. Monitor User Activity
Track all changes made on your site by using plugins like WP Activity Log. This helps you identify unusual behavior, such as unauthorized edits or suspicious login attempts.
Example: If a user with Editor privileges tries to modify admin-level settings, you’ll get notified immediately.
22. Implement a Web Application Firewall (WAF)
A Web Application Firewall (WAF) protects your site from a wide range of attacks, including SQL injection, cross-site scripting (XSS), and brute force. Services like Cloudflare or Sucuri offer robust WAF solutions for WordPress sites.
23. Enable Login Alerts
Receive notifications every time a user logs in from a new device or location. Plugins like Loginizer can send email alerts, helping you stay informed of unusual activity.
24. Enforce Strong Password Policies
Ensure that all users follow strong password policies. Use plugins like Password Policy Manager for WordPress to enforce rules, such as minimum character length and complexity requirements.
25. Set Session Expiration for Users
Automatically log out inactive users to minimize the risk of session hijacking. Plugins like Inactive Logout allow you to configure time limits for user sessions.
Example: A user who remains inactive for 15 minutes will be logged out, preventing potential misuse.
26. Limit User Roles and Privileges
Adopt the principle of least privilege by assigning users the minimum level of access they need to perform their roles. Regularly audit user permissions and remove unnecessary accounts or privileges.
27. Disable Pingbacks and Trackbacks
Pingbacks and trackbacks are often exploited for DDoS attacks. Disable them by navigating to Settings > Discussion in your WordPress dashboard and unchecking the relevant options.
28. Audit Plugins and Themes Regularly
Unused or outdated plugins and themes can become entry points for hackers. Conduct regular audits to identify and remove anything that’s no longer in use or unsupported by its developer.
Tip: Schedule plugin and theme reviews quarterly to ensure nothing slips through the cracks.
29. Use Database Prefix Changes
The default database prefix wp_ is commonly targeted in SQL injection attacks. Change it to something unique during installation or use a plugin like iThemes Security to update it later.
Example: Replace wp_ with a prefix like securedb_ for added security.
30. Deploy Security Headers
Security headers provide an additional shield against common vulnerabilities. Add the following headers to your .htaccess file or server configuration:
X-Frame-Options: DENYto prevent clickjacking.X-Content-Type-Options: nosniffto block MIME-type mismatches.Strict-Transport-Securityto enforce HTTPS.
Pro Tip: Use a plugin like HTTP Headers to implement these headers without manually editing files.
Proactive Monitoring and Education: Staying Ahead of Threats
Securing your WordPress site isn’t a one-time task—it’s an ongoing process. By adopting proactive monitoring and education practices, you can stay ahead of potential threats and ensure your site remains secure in the long run. The following strategies focus on regular oversight and building a security-conscious mindset.
31. Schedule Malware Scans
Regular malware scans help you detect and eliminate malicious code before it causes damage. Use plugins like Wordfence or Sucuri to automate daily or weekly scans.
32. Implement Content Security Policies (CSP)
A Content Security Policy (CSP) restricts the sources from which your website can load resources, such as scripts and images, preventing cross-site scripting (XSS) attacks. Use plugins like CSP Pro to configure your policy.
Pro Tip: Define trusted sources for your site’s scripts, styles, and media to minimize risks without affecting functionality.
33. Secure Admin Accounts
Avoid using generic usernames like “admin” for your administrator account. Opt for unique usernames that are harder to guess, and ensure all admin accounts have strong passwords.
Action Step: Regularly audit admin accounts to confirm they are in use and secured.
34. Disable Auto-Complete for Login Fields
Prevent browsers from saving login credentials by disabling the auto-complete feature. This ensures your site remains protected even if a device is compromised.
How-To: Add the following attribute to your login form’s HTML:
htmlCopy code<input type="password" autocomplete="off">
35. Perform Regular Security Audits
Hire professionals or use automated tools like WPScan or Nessus to conduct periodic security audits. These audits can uncover vulnerabilities and recommend fixes.
Frequency: Aim for quarterly audits or whenever significant changes are made to your site.
36. Educate Users on Security
Ensure all users with access to your WordPress site understand basic security principles. Provide training on identifying phishing attempts, using strong passwords, and safely managing credentials.
Example: Host a monthly security workshop or share regular security tips via email.
37. Secure Your Hosting Environment
Choose a hosting provider with built-in security features like malware scanning, DDoS protection, and automated backups. Look for providers that offer managed WordPress hosting for added peace of mind.
Recommended Hosts: Providers like SiteGround, Kinsta, and WP Engine are known for their robust security offerings.
38. Deploy Honeypots
Honeypots are traps that identify bots and malicious actors attempting to exploit your site. Use plugins like WP SpamShield or Anti-Spam Bee to deploy honeypots and reduce spam traffic.
Example: Honeypots can effectively block bots from submitting fake forms or engaging in brute-force attacks.
39. Test Your Site for Vulnerabilities
Regularly test your website using vulnerability scanners like WPScan or Nessus. These tools identify weaknesses and provide actionable recommendations.
Pro Tip: Run a scan after major updates or changes to ensure everything remains secure.
40. Subscribe to Security Alerts
Stay informed about the latest WordPress vulnerabilities by subscribing to security blogs, forums, or services like Patchstack and WordPress.org Security.
Bonus Tip: Join WordPress security groups or forums to share insights and learn from the community.
Conclusion: Building a Secure Future for Your WordPress Site
Your WordPress website is a valuable asset, and protecting it should be a top priority. This comprehensive security checklist for 2025 provides you with all the tools and knowledge you need to keep your site safe from evolving threats.
Whether you’re a seasoned developer or just starting out, these best practices are designed to be easy to implement and highly effective.
Don’t wait until it’s too late—start applying these security measures today to prevent potential breaches and ensure a smooth, secure experience for your users.