With over a decade of experience handling various types of websites, I’ve often heard people claim that WordPress sites are inherently insecure—that they have serious security issues and can be easily hacked. But that’s not quite true.
While nothing in this world is 100% secure, WordPress is no exception. However, its popularity speaks for itself: WordPress powers about 43% of all websites on the internet. Pretty impressive, right? But this widespread use also makes it a massive target for hackers seeking to hijack sites, steal sensitive data, or simply cause chaos for fun.
Bloggers, small business owners, eCommerce brands, and organizations alike invest hours creating blog posts, setting up online stores, or building portfolio sites—only to wake up one morning and find their site replaced with spammy ads promoting shady products. Yikes!
If you’ve ever wondered, “How do WordPress sites get hacked?”—you’re certainly not alone. Many site owners face this issue daily.
In this post, we’ll dive into 21 common vulnerabilities that can leave WordPress sites exposed, alongside real-life examples and practical tips to help you stay one step ahead of hackers. To learn more about another infamous Japanese Keyword Hack in detail, you can read this. Whether you’re a seasoned developer or just starting out, these insights will help you secure your digital space and sleep easier at night. Let’s get started!
21 Reasons Why WordPress Sites Get Hacked?
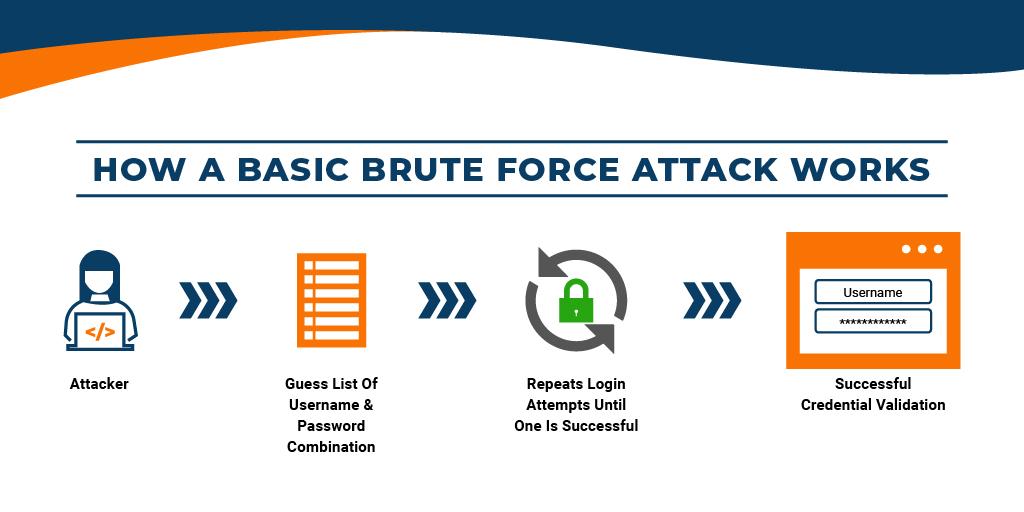
1. Brute Force Attacks
Ever watched a burglar trying every single key on the lock until something fits? That’s exactly what happens here, but digitally. Attackers run automated scripts that try millions of username and password combos until they stumble on the right one. It’s like a non-stop guessing game, and if your login details aren’t strong or unique enough, you’ll end up on the losing side.
In below image, you can see Brute force attacks use trial-and-error to guess logins, passwords, and other encrypted data.
How to Stay Safe:
- Use Strong Credentials: A long, quirky passphrase is way harder to crack than “123456” or “qwerty.”
- Limit Login Attempts: Plugins that block or lock out suspicious users after repeated failed logins can help.
- Enable Multi-Factor Authentication (MFA): Even if someone figures out your password, an extra verification step keeps them out.
- Hide Your Login Page: Changing the default “/wp-admin” URL can slow down attackers who rely on standard paths.
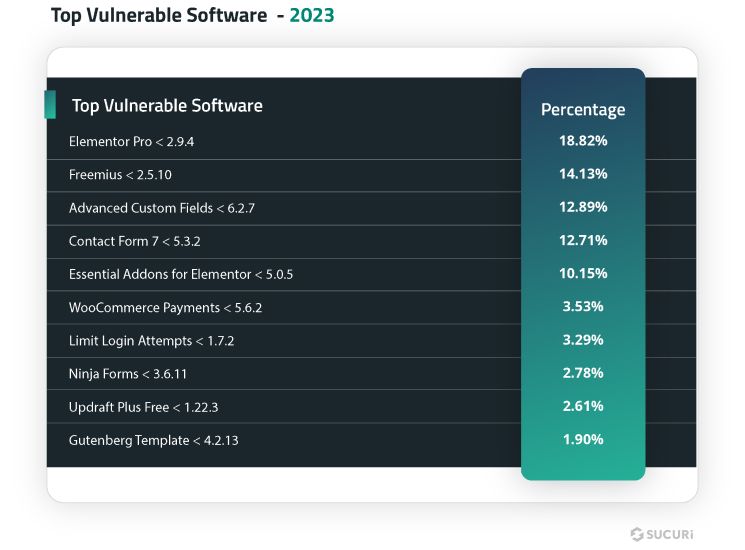
2. Vulnerable or Insecure Code in Plugins and Themes
Think of plugins and themes like the fancy gadgets and décor you add to your living room. They’re there to make everything look and feel great. But if they’re poorly made or left unattended, they can quietly open a backdoor for thieves. According to a report by Sucuri, a large chunk of hacked WordPress sites trace back to outdated or insecure third-party code.
How to Stay Safe:
- Stick to Trusted Sources: Install well-reviewed plugins and themes from reputable developers or official marketplaces.
- Keep Everything Updated: Outdated code can hold onto security flaws hackers already know how to exploit.
- Remove Unused Add-Ons: If you’re not actively using a plugin or theme, uninstall it to reduce potential weak points.
- Review Developer Reputation: Check how often updates are released, how quick the dev team is to patch issues, and how responsive they are to community feedback.
3. Cross-Site Scripting (XSS)
Cross site scripting (XSS) is a common attack vector that injects malicious code into a vulnerable web application. Attackers inject malicious scripts into web pages—often through poorly sanitized input fields—so that when unsuspecting visitors load the page, the harmful code runs in their browsers. XSS differs from other web attack vectors (e.g., SQL injections), in that it does not directly target the application itself. Instead, the users of the web application are the ones at risk. According to the OWASP Top 10 list, XSS/Injection consistently ranks as one of the most prevalent threats on the web.
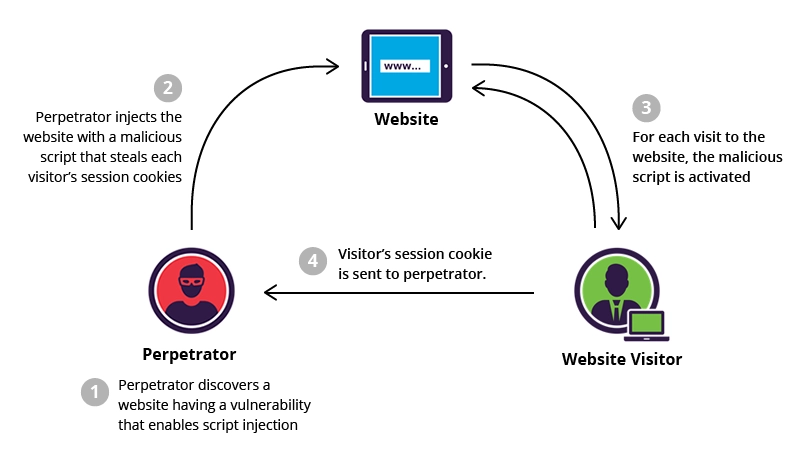
How to Stay Safe:
- Filter and Sanitize Inputs: Make sure form fields (like comments and contact forms) only accept the data you want.
- Use Trusted Security Plugins: Many WordPress security tools can detect and block suspicious scripts automatically.
- Check Theme and Plugin Code: Look out for echo or print functions that don’t sanitize user-supplied data.
- Educate Users: Encourage contributors and site members to be cautious when adding code snippets or HTML into content areas.
4. Phishing Attacks
Below is an example how phishing attacks can be used to hack your WordPress website.
Suppose, you received a message that appeared to be from your “hosting provider” asking you to verify billing details. It looked so legitimate that you clicked the link, entered your login info, and within minutes, the attackers are inside your WordPress dashboard, planting malicious scripts and redirecting visitors to sketchy websites.
In a nutshell, these scams rely on trust. Hackers pose as reliable brands or individuals, fooling people into handing over credentials, payment info, or other prized details.
How to Stay Safe:
- Double-Check the Sender: If that email urging you to “update now” comes from something like
info@secure-servicexx.cominstead of an official domain, think twice. - Hover Before You Click: Links can hide malicious URLs behind legit-looking text. Always hover to see where you’ll really end up.
- Use Spam Filters: Good email filters can block or flag most suspicious messages before they hit your inbox.
- Educate Your Team: One person clicking a bad link can topple your entire site. Train everyone to spot red flags—like awkward grammar or urgent scare tactics—and question any unexpected login requests.
5. Insecure File Permissions
Think of your website’s file system like the rooms in a house. If you give everyone a key to the main door (or worse, leave it wide open), you’ve practically invited strangers to poke around your stuff.

That’s what happens when your WordPress files and folders have overly generous permissions—like 777 (read, write, and execute for anyone). It may sound convenient, but it’s also a dream come true for intruders who can modify files at will or even plant malicious scripts.
How to Stay Safe:
- Stick to Secure Defaults: Typically, files should be at 644 and folders at 755—meaning not just anybody gets free rein.
- Use Your Hosting Panel Carefully: When you’re adjusting permissions via cPanel or FTP, double-check that you’re applying the correct settings.
- Scan Regularly: Security plugins or external scanners can spot unusual permission changes and alert you.
- Keep a To-Do Checklist: If you set a file to 777 for troubleshooting, remember to switch it back once you’re done.
6. Old or Unsecured Backup Files
When you leave backup files in a public folder on your server, unprotected and easily discoverable – it can be misused by hackers. They may download the archive which often contain critical data—like database credentials or sensitive user info—which is gold for cybercriminals. They’ll rummage through everything and use it to take over your site or even target your database directly.

How to Stay Safe:
- Store Backups Securely: Keep them off-site or at least protected by strong passwords and proper permissions.
- Delete What You Don’t Need: Old backups often pile up. Remove outdated ones so you don’t stack up unnecessary risk.
- Use Encrypted Solutions: Services that encrypt files before storage add an extra layer of defense.
- Check Visibility: Make sure backup directories aren’t publicly searchable through your domain (and block them with a simple .htaccess rule if needed).
7. Insider Threats (Compromised Workstation or Rogue Employees)
Sometimes, the biggest risk doesn’t come from faceless cybercriminals across the globe—it comes from inside your own walls. Maybe a well-meaning employee has a malware-infected laptop, or a disgruntled team member decides to poke around in places they shouldn’t. According to Ponemon Institute’s “Cost of Insider Threats” study, insider threats (both accidental and malicious) are on the rise, costing organizations millions each year.
Lets understand this with an example: At my agency, a former employee, who still had access to our WordPress admin panel, injected spam links into our website for their own benefit. We only realized this after some time had passed.
How to Stay Safe:
- Limit Access: Only grant each staff member the permissions they absolutely need.
- Enforce Strict Offboarding: The second someone leaves or changes roles, revoke their login rights.
- Secure Devices: Encourage everyone to install antivirus software and keep their operating systems updated.
- Audit Your Logs: Regularly check admin activity, login attempts, and file changes to catch anything fishy early.
8. Man-in-the-Middle (MITM) via Public Wi-Fi
We’ve all done it: you grab a latte at your favorite coffee shop, connect to the free Wi-Fi, and log right into your WordPress dashboard—totally unaware that someone else on that same network might be snooping.

If the connection isn’t encrypted or secured, hackers can tap into your session using tools like Wireshark or Cain & Abel, essentially hijacking your data (including login credentials). It’s like whispering your passwords in a crowded room; anybody listening can pick up the details.
How to Stay Safe:
- Only Use HTTPS/SSL: Make sure your site is secured so that any data exchanged is encrypted.
- Use a VPN: A Virtual Private Network scrambles your traffic, making it much harder for snoops to see what you’re doing.
- Avoid Logging In on Public Networks: If possible, wait until you’re on a trusted connection. If it’s urgent, consider changing your password once you’re safely off public Wi-Fi.
- Monitor Your Logs: Keep an eye out for unexpected or suspicious login attempts right after using public hotspots.
9. Multiple User Accounts with Poor Password Management
When a bunch of people log into the same website—like Admins, Editors, and Authors—it only takes one weak or shared password to compromise everything. It’s kind of like having the world’s safest house, but one roommate decides to leave the front door wide open every night. If someone uses “letmein” or “123456,” automated bots can crack that password in no time, giving them free rein over your content and data.
How to Stay Safe:
- Set Strict Policies: Insist on strong, unique passwords for every account—no exceptions.
- Limit User Roles: Don’t just hand out Admin access to everyone. Assign the least privileged role needed for each task.
- Implement Password Expiration: Ask team members to update their passwords regularly, especially if you suspect something fishy is going on.
- Use a Password Manager: Tools like LastPass or 1Password help everyone stay organized and avoid reusing the same weak login details.
10. Vulnerable Hosting Server
Even if your website has strong security, it can still be at risk if your hosting company has problems. If their servers aren’t updated or use old security methods, your website could be easily hacked.
This is especially true with shared hosting, where your website shares a server with others. If another website on that server is hacked, your website can also be affected, even if you did nothing wrong.
When your hosting company doesn’t keep things updated or doesn’t have good security measures, all the work you’ve done to protect your WordPress website can be wasted.
How to Stay Safe:
- Choose Reputable Hosts: Read reviews, check their security track record, and see how often they roll out updates.
- Ask About Security Features: Don’t be shy—ask potential hosts about their firewall, malware scanning, and SSL support.
- Keep Tabs on Server Updates: Stay informed of any scheduled maintenance or discovered vulnerabilities.
- Consider a Dedicated or VPS Plan: Shared hosting can be fine for smaller sites, but having a dedicated environment often comes with enhanced security measures.
11. Cross-Site Contamination
Ever tidy up your living room but leave the garage a total mess? Hackers can sneak in through that “messy” space and wind up trashing your spotless living room anyway.

In the context of WordPress, this happens when you’ve got multiple installations on the same server—maybe a test site or staging environment you haven’t updated in ages. Even if your main site is locked down tight, an outdated test or subdomain can serve as an accidental backdoor for attackers, letting them hop right over to your primary site.
How to Stay Safe:
- Keep Every Installation Updated: Don’t ignore subdomains or staging sites—treat them like your main site.
- Separate Environments: Whenever possible, use a different server or at least segregate staging and production sites.
- Delete Unused Sites: If you’re not using that old test setup anymore, get rid of it. Less clutter means fewer vulnerabilities.
- Scan Everything: Schedule routine malware scans across all your WordPress installations, not just the star attraction.
12. Weak Passwords or “admin” as Username
It’s surprising how many people still use the default “admin” username and pair it with a flimsy password like “12345” or “welcome.” That’s like rolling out the red carpet for intruders. Hackers typically start their brute force attempts by testing common login combinations, and “admin” plus an easy password often grants them instant access to your entire website.
How to Stay Safe:
- Pick a Unique Username: Swap out “admin” for something else—your site’s name, a play on words, or even your initials.
- Embrace Strong Passphrases: Combine random words, numbers, and symbols—something like “Bagel!M0jiForest.”
- Rotate Credentials: If you suspect a leak or notice any odd behavior, change your username and password right away.
- Enforce Policy Site-Wide: If you have multiple admins, make sure everyone follows the same security rules.
13. Stolen Session Cookies (Pass-the-Cookie Attack)
Ever handed someone your house key “just for a minute” and realized they might make a copy behind your back? That’s what happens when cybercriminals snatch your login session cookies from an infected device. These tiny files prove you’re already logged in, so the attacker can skip the usual username and password checks—just like they had a spare key to your front door.

How to Stay Safe:
- Protect Your Devices: Keep your antivirus up to date and run scans regularly to catch hidden malware.
- Log Out After Each Session: Especially on shared or public devices, make sure you actively click “log out” instead of closing the browser.
- Implement 2FA: With an extra verification factor, you can block attackers who try to piggyback on a stolen session.
- Avoid Storing Passwords in Plain Text: Encourage your team to use secure password managers rather than saving creds in a note on their desktop.
14. Social Engineering
Attackers don’t always need fancy hacking tools—they can just pretend to be a trusted contact, like your hosting provider or your IT support. They’ll use that fake identity to gather login credentials, convince you to install a “helpful” plugin (that’s actually malware), or fool you into giving them privileged access to your WordPress admin area. It’s astonishing how often people fall for these persuasive tactics when they’re caught off-guard or feeling rushed.
How to Stay Safe:
- Always Verify Identities: Double-check the source of any request. If your hosting provider calls, hang up and call them back on their official customer support line.
- Use a Zero-Trust Mindset: Treat every unexpected email or phone call with a dose of skepticism, especially if they ask for credentials.
- Train Your Team: Social engineering works best when people are unaware. Make sure your staff knows the red flags, such as urgent requests or requests for private info.
- Keep Communication Channels Clear: If you handle site emergencies through a specific channel—like a support ticket system—be consistent. Attackers often bank on catching you off-guard through less official routes.
15. SQL Injection
SQL injection occurs when attackers insert malicious SQL commands into input fields on websites, such as forms, URLs, or any other place where user input is accepted. If the website does not properly validate or sanitize this input, it may execute these commands directly on the underlying database. This can have serious consequences, allowing hackers to:
- Create new administrator accounts: Gaining unauthorized access and control over the website.
- Steal sensitive data: Access and exfiltrate personal information of users or confidential company data.
- Manipulate website content: Modify or delete existing content, potentially causing significant disruption or damage to the website’s reputation.
How to Stay Safe:
- Use Parameterized Queries: Don’t let your site mix code and user data in the same string. Prepared statements or parameterized queries can stop malicious injections.
- Sanitize and Validate Inputs: Make sure any data visitors enter—like search terms, contact forms, or registration info—is filtered for unexpected characters.
- Keep Core and Plugins Updated: Many default WordPress functions help protect against common injection attempts, but only if you’re running the latest versions.
- Deploy a Web Application Firewall (WAF): Tools like Cloudflare or Sucuri can filter out suspicious traffic that tries known SQL injection techniques.
16. Outdated WordPress Core
We’ve all been guilty of hitting the “Remind Me Later” button on a WordPress update. But leaving your website on an older version is like driving around with a flat tire—it’s bound to cause trouble sooner or later. Hackers actively hunt for known flaws in outdated core software because these vulnerabilities are public knowledge, making it a breeze to break in if you haven’t installed the latest patches.
How to Stay Safe:
- Enable Automatic Updates: Let WordPress handle minor updates on its own, so you’re not left exposed.
- Update Promptly: When a new version is released—especially a security patch—don’t drag your feet.
- Test on a Staging Site: If you’re worried about compatibility issues, try updates on a test environment first.
- Regularly Check for Compatibility: Make sure your plugins and themes also support the latest WordPress version so everything stays in sync.
17. Missing or Weak Two-Factor Authentication (2FA/MFA)
Adding 2FA or MFA is like installing a second, extra-secure lock that only you can open—maybe with a fingerprint, a special code, or an authenticator app. Without it, all hackers need is your password, and if they manage to guess or steal it, they’re basically home free.
How to Stay Safe:
- Enable 2FA: WordPress plugins or third-party services can send a code to your phone or generate app-based tokens.
- Use an Authenticator App: Apps like Google Authenticator or Authy are way more secure than SMS-based codes.
- Encourage Your Team: Make 2FA mandatory for everyone with access, not just admins.
- Review Regularly: Check that 2FA is working correctly and remind users to keep their phones and backup codes safe.
18. Directory Browsing Enabled
When directory browsing is turned on, hackers can easily peek into your website’s file structure, discovering sensitive files like backups, configuration files, or even hidden admin folders. It’s like giving intruders a detailed map of your digital home, making it much easier for them to find weak spots to exploit.
How to Stay Safe:
- Disable Directory Browsing: The simplest way to prevent unauthorized access is to turn off directory browsing. You can do this by adding
Options -Indexesto your.htaccessfile. - Use a Robust .htaccess File: Protect sensitive directories by restricting access through your
.htaccessfile. For example, you can deny all access to thewp-includesfolder, which houses many of WordPress’s core files. - Keep Your Files Organized: Avoid cluttering your server with unnecessary files or outdated backups in publicly accessible directories. Instead, store backups securely off-site or in non-public folders.
- Regular Security Audits: Periodically check your website’s directory structure to ensure there are no exposed folders or files that could provide hackers with a roadmap to your site’s vulnerabilities.
- Employ Security Plugins: Utilize WordPress security plugins like Wordfence or Sucuri that can help monitor and block suspicious activities related to directory browsing attempts.
19. Cross-Site Request Forgery (CSRF)
Imagine you’re at a bustling restaurant, and someone slips a note to the waiter asking for an extra dessert on your tab without you noticing. Suddenly, you’re paying for something you never ordered. That’s pretty much what Cross-Site Request Forgery (CSRF) does to your WordPress site.
It tricks your browser into performing unwanted actions on a website where you’re already authenticated. In simpler terms, if you’re logged into your WordPress admin panel and visit a malicious site, that site could send commands to your WordPress site without you realizing it. It’s like someone hijacking your actions behind the scenes.
How to Stay Safe:
- Use Security Tokens: Implement nonces (numbers used once) in your forms and URLs. These tokens ensure that the request is coming from a legitimate source and not a malicious site trying to trick your browser.
- Verify Referrer Headers: Check the HTTP referrer header to ensure that the request is coming from your own site. If it’s not, block the action.
- Limit User Permissions: Only give necessary permissions to users. The fewer privileges a user has, the less damage a potential CSRF attack can cause.
- Implement SameSite Cookies: This cookie attribute restricts how cookies are sent with cross-site requests, adding an extra layer of protection against CSRF attacks.
- Educate Your Team: Make sure everyone understands what CSRF is and how to recognize suspicious activities. Awareness is a powerful tool in preventing these kinds of attacks.
20. Not Using SSL/HTTPS
When your WordPress site doesn’t use SSL (Secure Sockets Layer) or HTTPS (HyperText Transfer Protocol Secure) – all data exchanged between your website and its visitors travels in plain text, making it a breeze for hackers to snoop on sensitive information like login credentials, credit card details, and personal data.
How to Stay Safe:
- Install an SSL Certificate: This is your first line of defense. SSL encrypts the data between your site and its visitors, ensuring that sensitive information remains private. Many hosting providers offer free SSL certificates through services like Let’s Encrypt.
- Always Use HTTPS: Make sure your website is accessible via HTTPS rather than just HTTP. You can set up automatic redirects from HTTP to HTTPS to ensure every visitor lands on the secure version of your site.
- Update Internal Links: After switching to HTTPS, update all internal links, images, and resources to use the secure protocol. This prevents mixed content warnings and ensures a fully secure browsing experience.
- Enable HSTS (HTTP Strict Transport Security): This tells browsers to always use HTTPS when communicating with your site, even if users type in HTTP. It adds an extra layer of protection against certain types of attacks.
- Monitor Your SSL Status: Use online tools like SSL Labs’ SSL Test to regularly check your SSL configuration and ensure there are no vulnerabilities or misconfigurations.
- Educate Your Team: Make sure everyone involved with your website understands the importance of SSL and HTTPS. Encourage best WordPress security practices, like always checking for the secure padlock icon before entering sensitive information.
21. Zero-Day Exploits
Zero-day exploit are brand-new vulnerabilities that hackers discover before the WordPress community even knows they exist. Since there’s no patch or fix available yet, these exploits can wreak havoc without warning.
How to Stay Safe:
- Stay Informed: Keep up with the latest security news and updates related to WordPress. Subscribing to reputable security blogs or newsletters can help you stay ahead of emerging threats.
- Implement a Web Application Firewall (WAF): A WAF like Cloudflare or Sucuri can help block malicious traffic and filter out suspicious activities, providing an extra layer of defense against unknown exploits.
- Regular Security Scans: Use security plugins or external services to perform regular scans of your website. These tools can help detect unusual behavior or signs of compromise early on.
- Backup Frequently: Maintain regular backups of your site, including databases and files. In the event of an exploit, having recent backups allows you to restore your site quickly with minimal data loss.
- Limit Plugin and Theme Use: The more plugins and themes you have, the more potential vulnerabilities exist. Use only trusted, essential plugins and keep them updated to reduce the attack surface.
- Develop a Quick Response Plan: Have a plan in place for when a zero-day exploit is discovered. This should include steps for isolating the affected site, communicating with stakeholders, and implementing temporary fixes until an official patch is released.
- Use Security Plugins: Plugins like Wordfence or iThemes Security offer features that can help protect your site against a variety of threats, including zero-day exploits, by monitoring for suspicious activity and enforcing strict security measures.
That’s all in the article. I hope it will prevent your WordPress site from getting hacked.
Just remember that the landscape of cybersecurity is always evolving. New threats emerge, and hackers become smarter. That’s why it’s crucial to stay informed, keep your WordPress site up-to-date, and continuously assess your security posture.
Don’t wait until something goes wrong—take proactive steps today to safeguard your website, your data, and your peace of mind.